You like weird bugs involving shell implementations, syscalls and filesystems? Somehow I do, this was an interesting one.
I like this kind of oddities in languages. This is nice to see such a list for Rust at a single place.
This piece is a bit too much written as Rust zealotry for my taste. That being said, there's in my opinion an interesting core truth hidden in there: for now it seems to better foster "expert generalists" when investing in it. Now it might be just for now and might stop later... time will tell.
Yes, tests can follow patterns as well... and antipatterns too. It's good to name those antipatterns, let's avoid them shall we?
Interesting framework to reason about lock-ins. It's not only about depending on a vendor, there are other factors to keep in mind. Now obviously I'd see the risks around cloud hosting in particular in a different way than the author... but I guess we're biased differently there.
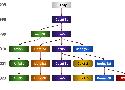
A bit old perhaps, but shows quite well the various options to pass a function around in C++.
This is a model which seems to work for donation campaigns for FOSS projects. I wonder how much this scales though... if everyone does that, is there a point where users will be fed up with it?
uv really opens the door to nice features for Python. Now with a standardized PEP to help the configuration it's getting even better.
Nice! At last a Makefile linter. It has some interesting features, I especially like the automated .PHONY target management.
The situation around OpenSSL and its fork is rather confusing... And there's no indication this would improve.
Nice explanation of how graph search algorithms work. If you need to build some path finding feature this is for you.
A good reminder that "push it to the GPU and it'll be faster" isn't true. If you move a workload to the GPU you likely have to rethink quite a bit how it's done.
I like this article. Indeed, focus on building organisations and teams where it's easy to do the right thing bit hard to fail. This is much better than obsessing over mythical 10x engineers.
There are indeed fields where this matters a lot. It is far from being an easy problem to solve though.
We can expect this to be a game changer for the C++ ecosystem. A couple of examples are presented in this article.
Interesting comparison, indeed would a clock like this be useful?
It's indeed difficult to separate FUD from the real community issues around Matrix right now. We'll have to keep an eye on how things evolve.
Definitely this, as projects scale, keeping an eye on dependencies between teams is key to efficient allocation. This will happen by trying to eliminate said dependencies, reallocating between teams.
The Adaptive Model is a lesser known design pattern. Like any other pattern make sure you are in the right context to introduce it. Especially this one as it can get really verbose. This article shows a refactoring path for moving from imperative logic to adaptive model.
Since the movie became fashionable again, it might be interesting to go through this piece. The movie wasn't great, the article is a bit of a stretch... but at times it tells something about what's required to master a craft. It's a funny and short piece.